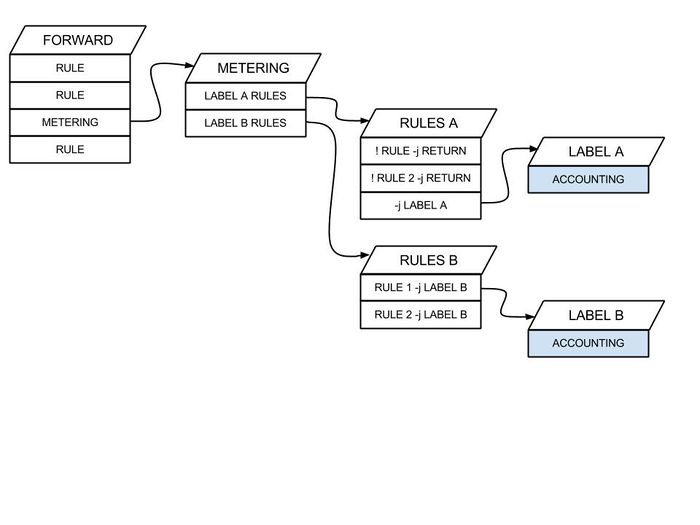
From this
We can use the neutron command to list the related metering rules and labels
$ neutron meter-label-list
$ neutron meter-label-rule-list
The "neutron-meter-agent" will collect the traffic accounting in the
root@sn1
root@sn1

root@sn1
root@node-5

root@node-5

root@node-5

So, we need to find the metering labels: "neutron-meter-l-78675a84" and "neutron-meter-l-b88c5977"
root@cn3:~# ip netns exec qrouter-b1741371-ee12-46a1-831b-d3b35429d7c8 iptables -nL -v -x

root@cn3:~# ip netns exec qrouter-b1741371-ee12-46a1-831b-d3b35429d7c8 iptables -t nat -S

Here is the example to query the metering data in Ceilometer
$ root@node-5:~# ceilometer statistics -m bandwidth -q "resource=b88c5977-4445-4f19-9c8f-3d92809f844e;timestamp>=2016-03-01T00:00:00" --period 86400
P.S:
The following article is to introduce "Traffic Accounting with Linux IPTables" which can make us
http://www.catonmat.net/blog/traffic-accounting-with-iptables/
https://wiki.openstack.org/wiki/Neutron/Metering/Bandwidth