netfilter-like kernel module to get source and destination address
b.attach_kprobe(event="ip_local_deliver_finish", fn_name="trace_nf_local_in")
func netns ifname saddr sport srcmac daddr dport dstmac seq ack flag tcplen user_data_hex
local_in 0 eth0 10.217.1.195 42252 46:aa:dd:21:3d:26 10.217.1.112 80 2a:7f:54:c6:ab:af 4204670713 0 2 0
local_in 0 eth0 10.106.186.19 80 2e:05:a8:fd:7f:a3 10.217.1.195 42252 02:80:c5:35:36:fe 3808943125 4204670714 18 0
local_in 0 eth0 10.217.1.195 42252 46:aa:dd:21:3d:26 10.217.1.112 80 2a:7f:54:c6:ab:af 4204670714 3808943126 16 0
local_in 0 eth0 10.217.1.195 42252 46:aa:dd:21:3d:26 10.217.1.112 80 2a:7f:54:c6:ab:af 4204670714 3808943126 24 118 504f5354202f76312f726571756573742d6c616e64696e6720485454502f312e310d0a486f73743a206465617468737461722e64656661756c742e7376632e636c75737465722e6c6f63616c0d0a557365722d4167656e743a206375726c2f372e35322e310d0a4163636570743a202a2f2a0d0a0d0a
local_in 0 eth0 10.106.186.19 80 2e:05:a8:fd:7f:a3 10.217.1.195 42252 02:80:c5:35:36:fe 3808943126 4204670832 16 0
local_in 0 eth0 10.106.186.19 80 2e:05:a8:fd:7f:a3 10.217.1.195 42252 02:80:c5:35:36:fe 3808943126 4204670832 24 114 485454502f312e3120323030204f4b0d0a436f6e74656e742d547970653a20746578742f706c61696e0d0a446174653a205765642c2031362044656320323032302030313a32313a313120474d540d0a436f6e74656e742d4c656e6774683a2031320d0a0d0a53686970206c616e6465640a
local_in 0 eth0 10.217.1.195 42252 46:aa:dd:21:3d:26 10.217.1.112 80 2a:7f:54:c6:ab:af 4204670832 3808943240 16 0
local_in 0 eth0 10.217.1.195 42252 46:aa:dd:21:3d:26 10.217.1.112 80 2a:7f:54:c6:ab:af 4204670832 3808943240 17 0
local_in 0 eth0 10.106.186.19 80 2e:05:a8:fd:7f:a3 10.217.1.195 42252 02:80:c5:35:36:fe 3808943240 4204670833 17 0
local_in 0 eth0 10.217.1.195 42252 46:aa:dd:21:3d:26 10.217.1.112 80 2a:7f:54:c6:ab:af 4204670833 3808943241 16 0
b.attach_kprobe(event="ip_local_out", fn_name="trace_nf_local_out")
func netns ifname saddr sport srcmac daddr dport dstmac seq ack flag tcplen user_data_hex
local_out 4026532650 10.217.1.195 56602 00:00:00:00:00:00 10.106.186.19 80 00:00:00:00:00:00 1392073873 0 2 0
local_out 4026532715 10.217.1.112 80 8c:ff:ff:00:1c:e9 10.217.1.195 56602 00:00:1c:e9:43:a0 1492739806 1392073874 18 0
local_out 4026532650 10.217.1.195 56602 00:00:00:00:00:00 10.106.186.19 80 00:00:00:00:00:00 1392073874 1492739807 16 0
local_out 4026532650 10.217.1.195 56602 2f:2e:2e:2f:2e:2e 10.106.186.19 80 00:2e:2e:2f:2e:2e 1392073874 1492739807 24 118 504f5354202f76312f726571756573742d6c616e64696e6720485454502f312e310d0a486f73743a206465617468737461722e64656661756c742e7376632e636c75737465722e6c6f63616c0d0a557365722d4167656e743a206375726c2f372e35322e310d0a4163636570743a202a2f2a0d0a0d0a
local_out 4026532715 10.217.1.112 80 8c:ff:ff:00:1c:e9 10.217.1.195 56602 00:00:1c:e9:43:a0 1492739807 1392073992 16 0
local_out 4026532715 10.217.1.112 80 2f:2e:2e:2f:2e:2e 10.217.1.195 56602 00:2e:2e:2f:2e:2e 1492739807 1392073992 24 114 485454502f312e3120323030204f4b0d0a436f6e74656e742d547970653a20746578742f706c61696e0d0a446174653a205765642c2031362044656320323032302030323a30383a323220474d540d0a436f6e74656e742d4c656e6774683a2031320d0a0d0a53686970206c616e6465640a
local_out 4026532650 10.217.1.195 56602 8c:ff:ff:00:1c:e9 10.106.186.19 80 00:00:1c:e9:43:a0 1392073992 1492739921 16 0
local_out 4026532650 10.217.1.195 56602 8c:ff:ff:00:1c:e9 10.106.186.19 80 00:00:1c:e9:43:a0 1392073992 1492739921 17 0
local_out 4026532715 10.217.1.112 80 00:00:00:00:00:00 10.217.1.195 56602 00:00:00:00:00:00 1492739921 1392073993 17 0
local_out 4026532650 10.217.1.195 56602 8c:ff:ff:00:1c:e9 10.106.186.19 80 00:00:1c:e9:43:a0 1392073993 1492739922 16 0
b.attach_kprobe(event="ip_finish_output2", fn_name="trace_nf_local_out")
func netns ifname saddr sport srcmac daddr dport dstmac seq ack flag tcplen user_data_hex
local_out 4026532650 eth0 10.217.1.195 58332 00:00:00:00:00:00 10.106.186.19 80 00:01:46:00:00:00 3689919668 0 2 0
local_out 4026532780 eth0 10.217.1.169 80 00:00:00:00:00:00 10.217.1.195 58332 00:00:00:00:00:00 201303256 3689919669 18 0
local_out 4026532650 eth0 10.217.1.195 58332 00:00:00:00:00:00 10.106.186.19 80 00:01:46:00:00:00 3689919669 201303257 16 0
local_out 4026532650 eth0 10.217.1.195 58332 8c:ff:ff:00:00:00 10.106.186.19 80 00:68:8d:f6:f9:a0 3689919669 201303257 24 118 504f5354202f76312f726571756573742d6c616e64696e6720485454502f312e310d0a486f73743a206465617468737461722e64656661756c742e7376632e636c75737465722e6c6f63616c0d0a557365722d4167656e743a206375726c2f372e35322e310d0a4163636570743a202a2f2a0d0a0d0a
local_out 4026532780 eth0 10.217.1.169 80 00:00:00:00:00:00 10.217.1.195 58332 00:00:00:00:00:00 201303257 3689919787 16 0
local_out 4026532780 eth0 10.217.1.169 80 8c:ff:ff:00:00:00 10.217.1.195 58332 00:68:8d:f6:f9:a0 201303257 3689919787 24 114 485454502f312e3120323030204f4b0d0a436f6e74656e742d547970653a20746578742f706c61696e0d0a446174653a205765642c2031362044656320323032302030323a31343a313320474d540d0a436f6e74656e742d4c656e6774683a2031320d0a0d0a53686970206c616e6465640a
local_out 4026532650 eth0 10.217.1.195 58332 00:00:00:00:00:00 10.106.186.19 80 00:00:00:00:00:00 3689919787 201303371 16 0
local_out 4026532650 eth0 10.217.1.195 58332 00:00:00:00:00:00 10.106.186.19 80 00:00:00:00:00:00 3689919787 201303371 17 0
local_out 4026532780 eth0 10.217.1.169 80 00:00:00:00:00:00 10.217.1.195 58332 00:01:46:00:00:00 201303371 3689919788 17 0
local_out 4026532650 eth0 10.217.1.195 58332 00:00:00:00:00:00 10.106.186.19 80 00:00:00:00:00:00 3689919788 201303372 16 0
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.217.1.195", "sport": 41440, "srcmac": "02:80:c5:35:36:fe", "daddr": "10.106.186.19", "dport": 80, "dstmac": "", "seq": 3827905078, "ack": 0, "flags": 2, "tcplen": 0, "user_data_hex": ""}
{"name": "local", "saddr": "10.217.1.112", "sport": 80, "srcmac": "2a:7f:54:c6:ab:af", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "", "seq": 3863923945, "ack": 3827905079, "flags": 18, "tcplen": 0, "user_data_hex": ""}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.106.186.19", "sport": 80, "srcmac": "", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "02:80:c5:35:36:fe", "seq": 3863923945, "ack": 3827905079, "flags": 18, "tcplen": 0, "user_data_hex": ""}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.217.1.195", "sport": 41440, "srcmac": "02:80:c5:35:36:fe", "daddr": "10.106.186.19", "dport": 80, "dstmac": "", "seq": 3827905079, "ack": 3863923946, "flags": 16, "tcplen": 0, "user_data_hex": ""}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.217.1.195", "sport": 41440, "srcmac": "02:80:c5:35:36:fe", "daddr": "10.106.186.19", "dport": 80, "dstmac": "", "seq": 3827905079, "ack": 3863923946, "flags": 24, "tcplen": 118, "user_data_hex": "504f5354202f76312f726571756573742d6c616e64696e6720485454502f312e310d0a486f73743a206465617468737461722e64656661756c742e7376632e636c75737465722e6c6f63616c0d0a557365722d4167656e743a206375726c2f372e35322e310d0a4163636570743a202a2f2a0d0a0d0a"}
{"name": "local", "saddr": "10.217.1.112", "sport": 80, "srcmac": "2a:7f:54:c6:ab:af", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "", "seq": 3863923946, "ack": 3827905197, "flags": 16, "tcplen": 0, "user_data_hex": ""}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.106.186.19", "sport": 80, "srcmac": "", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "02:80:c5:35:36:fe", "seq": 3863923946, "ack": 3827905197, "flags": 16, "tcplen": 0, "user_data_hex": ""}
{"name": "local", "saddr": "10.217.1.112", "sport": 80, "srcmac": "2a:7f:54:c6:ab:af", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "", "seq": 3863923946, "ack": 3827905197, "flags": 24, "tcplen": 114, "user_data_hex": "485454502f312e3120323030204f4b0d0a436f6e74656e742d547970653a20746578742f706c61696e0d0a446174653a205765642c2031362044656320323032302030313a31383a333420474d540d0a436f6e74656e742d4c656e6774683a2031320d0a0d0a53686970206c616e6465640a"}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.106.186.19", "sport": 80, "srcmac": "", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "02:80:c5:35:36:fe", "seq": 3863923946, "ack": 3827905197, "flags": 24, "tcplen": 114, "user_data_hex": "485454502f312e3120323030204f4b0d0a436f6e74656e742d547970653a20746578742f706c61696e0d0a446174653a205765642c2031362044656320323032302030313a31383a333420474d540d0a436f6e74656e742d4c656e6774683a2031320d0a0d0a53686970206c616e6465640a"}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.217.1.195", "sport": 41440, "srcmac": "02:80:c5:35:36:fe", "daddr": "10.106.186.19", "dport": 80, "dstmac": "", "seq": 3827905197, "ack": 3863924060, "flags": 16, "tcplen": 0, "user_data_hex": ""}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.217.1.195", "sport": 41440, "srcmac": "02:80:c5:35:36:fe", "daddr": "10.106.186.19", "dport": 80, "dstmac": "", "seq": 3827905197, "ack": 3863924060, "flags": 17, "tcplen": 0, "user_data_hex": ""}
{"name": "local", "saddr": "10.217.1.112", "sport": 80, "srcmac": "2a:7f:54:c6:ab:af", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "", "seq": 3863924060, "ack": 3827905198, "flags": 17, "tcplen": 0, "user_data_hex": ""}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.106.186.19", "sport": 80, "srcmac": "", "daddr": "10.217.1.195", "dport": 41440, "dstmac": "02:80:c5:35:36:fe", "seq": 3863924060, "ack": 3827905198, "flags": 17, "tcplen": 0, "user_data_hex": ""}
{"name": "k8s_spaceship_tiefighter_default_86a21ead-837e-4984-83ee-15741b91dfab_1", "saddr": "10.217.1.195", "sport": 41440, "srcmac": "02:80:c5:35:36:fe", "daddr": "10.106.186.19", "dport": 80, "dstmac": "", "seq": 3827905198, "ack": 3863924061, "flags": 16, "tcplen": 0, "user_data_hex": ""}
Linux Kernel Communication — Netfilter Hooks


k8s網路資料包流程
iptables DNAT 與SNAT 詳解
Layer 3 IP Stack
洞悉linux下的Netfilter&iptables:网络地址转换原理之DNAT
洞悉linux下的Netfilter&iptables:網絡地址轉換原理之SNAT
Linux數據包的接收與發送過程
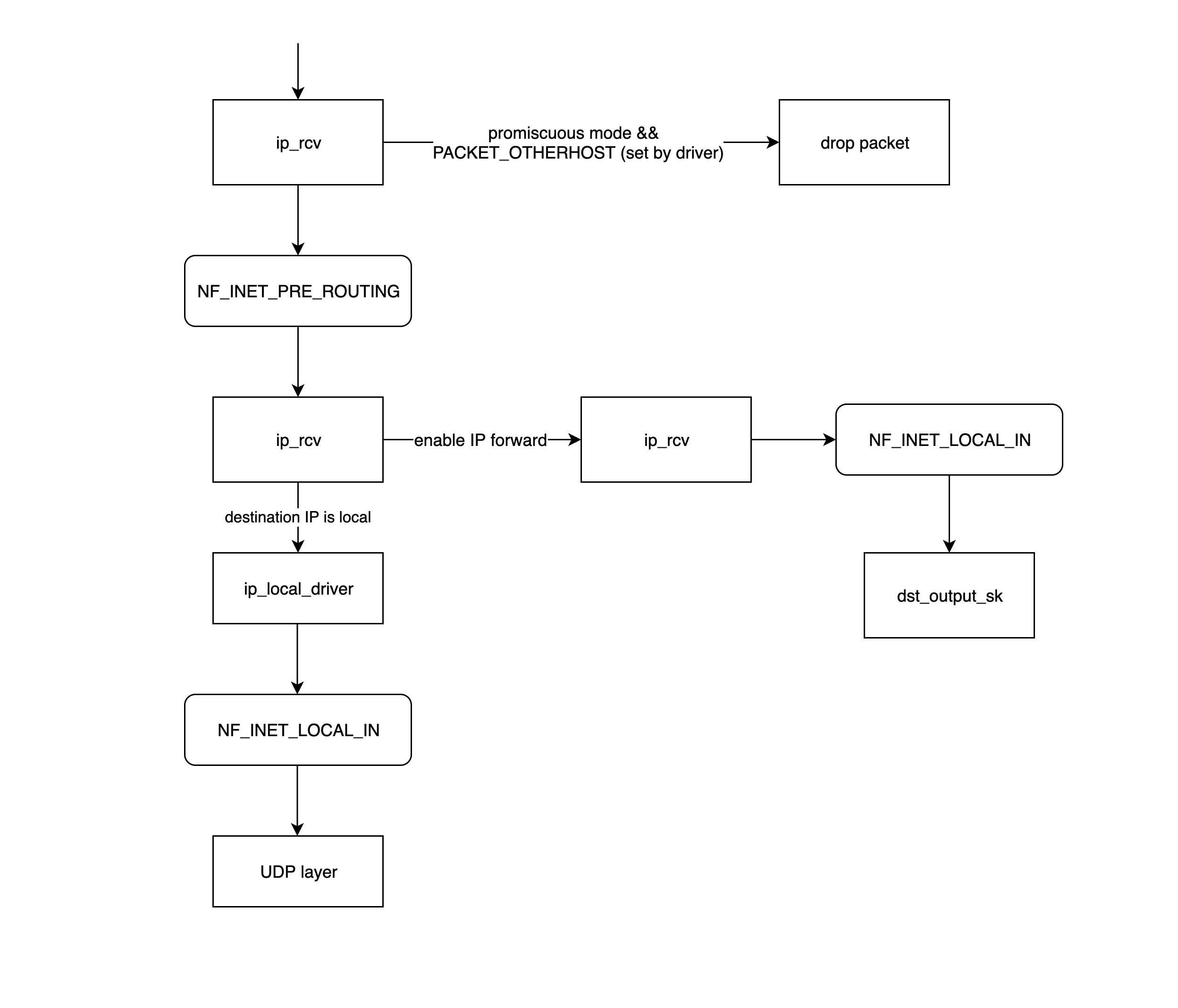
Linux網絡- 數據包的接收過程
|
|
↓ promiscuous mode &&
+--------+ PACKET_OTHERHOST (set by driver) +-----------------+
| ip_rcv |-------------------------------------->| drop this packet|
+--------+ +-----------------+
|
|
↓
+---------------------+
| NF_INET_PRE_ROUTING |
+---------------------+
|
|
↓
+---------+
| | enabled ip forword +------------+ +----------------+
| routing |-------------------->| ip_forward |------->| NF_INET_FORWARD |
| | +------------+ +----------------+
+---------+ |
| |
| destination IP is local ↓
↓ +---------------+
+------------------+ | dst_output_sk |
| ip_local_deliver | +---------------+
+------------------+
|
|
↓
+------------------+
| NF_INET_LOCAL_IN |
+------------------+
|
|
↓
+-----------+
| UDP layer |
+-----------+
Linux 网络层收发包流程及 Netfilter 框架浅析
No comments:
Post a Comment